Key Takeaways
- Point-of-sale (POS) security operates through a combination of hardware and software protections designed to prevent unauthorized access and data theft.
- A well-planned POS security includes multi-layered programs, such as encryption, tokenization, and network segmentation.
- Businesses should also be prepared with an incident response plan in the event of a data breach.
- Strengthening POS security is not only essential for data protection but also for maintaining customer trust and regulatory compliance.
At the core of every business operation is a POS system. In addition to processing transactions, POS systems also store customer-sensitive information and integrate all other business management tools into a single hub. Unfortunately, this makes POS systems prime targets for cybercriminals looking to steal business intelligence, credit card information, and personal data. Without reliable POS security, businesses are in danger of data breaches, which can lead to financial losses, reputational damage, and legal repercussions.
What is POS security?
POS security is a collection of strategies, technologies, and best practices designed to safeguard POS from cyber threats. Given that POS terminals handle sensitive payment information, multiple security measures must be in place to prevent data breaches and ensure compliance with industry regulations.
Effective POS security is not just about installing the most advanced anti-malware software in the market. It also requires a complete understanding of your business network system that will allow you to identify every access point that hackers may exploit. This includes everything from your customer’s use of mobile devices to make payments to your employee’s use of company email.
How does POS security work?
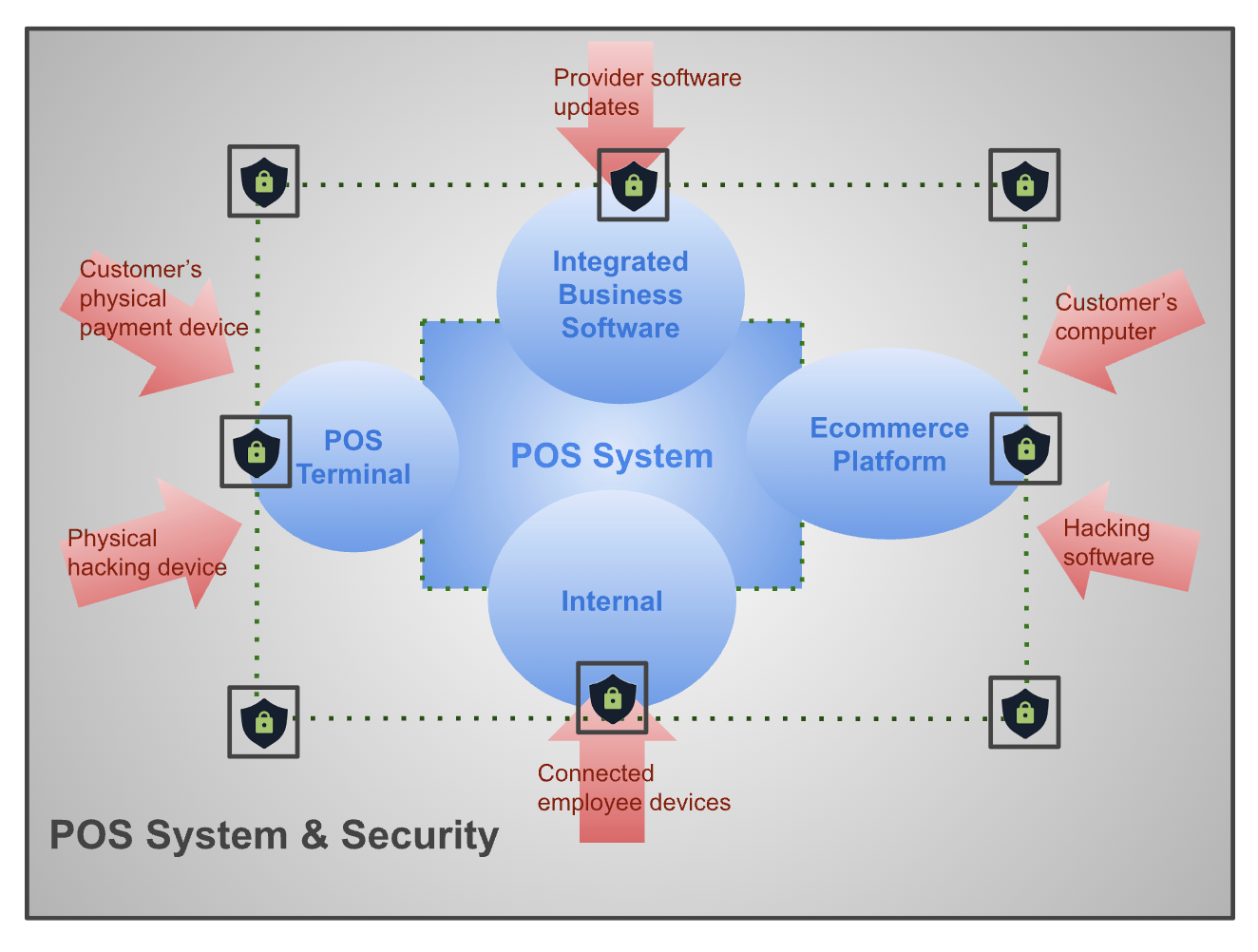
The POS system has multiple direct access points — POS terminals, ecommerce websites, and merchant dashboards — as well as indirect channels that eventually give them access to your POS system. This includes piggybacking their hacking programs on legitimate connections, such as company computers and integrated third-party software.
To address these vulnerabilities, businesses set up multiple layers of securities beginning with a built-in fraud protection program and network firewall that protects every device and platform connected to your POS system.
While there are many sophisticated POS security strategies, each one will include the following key components:
- End-to-end encryption (E2EE): Converts plaintext data into an unreadable format called ciphertext from the moment it is entered from the payment gateway until it reaches the payment processor, preventing interception.
- Tokenization: Replaces sensitive cardholder data with unique tokens that reference the sensitive data but have no intrinsic value, making it useless to hackers.
- Network segmentation: While a POS system is interconnected with the rest of the company’s network, the infrastructure operates in smaller segments with its own security measures to reduce exposure to threats.
- User authentication and access control: Restricts POS access points with protocols, such as passwords, multi-factor authentication (MFA), challenge-response tests like CAPTCHA, and role-based permissions.
- Intrusion detection systems (IDS): Monitors POS networks for suspicious activity and potential breaches from known POS malware.
- Network firewall: Security program that controls network access based on established company security policies.
- Regular software updates and patch management: Ensures POS applications are regularly updated with security patches that allow their internal fraud protection tools to recognize the latest cyber threats.
In addition to internal security policies, businesses also require their partners that have access to their systems to meet compliance with industry regulations such as the Payment Card Industry Data Security Standard (PCI DSS).
Related: What is PCI Compliance?
Common POS security threats
Below are some of the most common threats along with real-life incidents that show how data breaches impact business operations:
- Malware attacks: Cybercriminals use malware to infiltrate POS systems and steal payment data. Ransomware is a type of malware virus.
Example: January 2025, Lowe Engineers, based out of Atlanta, Georgia became victim to ransomware Lynx, which resulted in the compromise of confidential engineering project information and client data.
- Skimming: Use of a physical device (attached to a POS terminal) or a set of malicious codes used to steal cardholder information.
Example: In May 2024, ALDI, a large supermarket chain, published a notice of data breach on its website. Card skimming devices were discovered in five of its locations.
Example: In Jan 2022, cybercriminals managed to embed a Magecart skimmer within Segway’s online store code that captured credit card data while customers entered their information on the website’s online checkout.
- Phishing: Cyber attacks that are meant to trick individuals into clicking on malicious links. These links redirect victims to spoof websites or embed malicious software in the user’s computer in an attempt to steal sensitive data.
Example: In February 2024, Change Healthcare, fell victim to a phishing attack, capturing a user’s login credentials. This resulted in an estimated $1.6 billion in cost and 100 million users of the company’s services affected.
- Brute force attack: A method used by cybercriminals to gain unauthorized access through using an algorithm that can generate all possible password combinations.
Example: In 2016, Dunkin’ Donuts paid $650,000 in fines and damages due to a brute force attack that gave hackers access to more than 300,000 user account information until 2018.
See: How Much Time Does it Take for Hackers to Crack My Password?
- Insider threats: Employees with access to POS systems may intentionally or unintentionally compromise security.
Example: In May 2023, two former Tesla employees leaked 75,000 sensitive personal data of current and former employees to a foreign media outlet. The breach also included Tesla production secrets and complaints about Tesla’s full self-driving features.
Understanding these threats helps businesses implement proactive POS security measures and protect customer data from evolving cyber risks.
Related: POS Terminals Explained By Experts
Enhancing your POS security in 4 steps
Securing your POS system requires a proactive approach with multiple layers of defense. Here are four steps to enhancing your POS security:
1. Conduct regular risk assessment
Regularly evaluate potential security vulnerabilities within your POS infrastructure, covering hardware, software, and network configurations.
- Hardware and software: Ensure that all operating systems and applications are updated to patch security flaws. Enable encryption, restrict internet-facing components, and replace default passwords with stronger credentials.
- Network configuration: Assess wired and wireless networks, implementing firewalls and secure WiFi passphrases. If possible, limit signal range to prevent unauthorized access.
- Store layout: Position POS terminals away from entry points and install security cameras strategically, to monitor for tampering, avoiding blindspots at the checkout counter.
- Data security practices: Apply the principle of least privilege in security access, encrypt sensitive data, maintain access logs, and schedule regular backups.
- Unexpected threats: Conduct security audits to check for skimming devices on POS terminals and potential third-party vulnerabilities that could expose your system to cyber threats.
2. Implement POS security best practices
Refer to data security industry guidelines, such as the PCI DSS, to establish best practices based on your current business needs. This should include a combination of strategies to protect both physical and software infrastructure of your POS system.
- Use dedicated terminals: Restrict POS processing to dedicated devices that are protected by fraud monitoring and prevention tools rather than shared systems.
- Encrypt sensitive data: Use strong encryption protocols to protect payment card data in storage or transit, making it unreadable to cyber criminals.
- Set employee permissions: Implement role-based access control (RBAC) to limit user permissions based on job functions and monitor access logs to detect suspicious activity.
- Install and maintain a network firewall: A properly configured firewall acts can restrict unauthorized access and prevent hackers from retrieving sensitive information.
- Immediately install software security updates: Regularly update POS software, firewalls, and antivirus programs. Automate updates where possible to prevent vulnerabilities from remaining unpatched.
- Train your employees: Conduct data security training, particularly for new hires. Consider an annual refresher on the immediate steps in case of a data breach. Document your training and strategies and file where employees can get access on a regular basis.
- Observe PCI compliance: Adhere to PCI DSS requirements, including installing antivirus software, using EMV payment tools, and monitoring for skimming devices.
Also see: Point of Sale Security Guide and Checklist
3. Choose a reputable POS security provider
Choosing the right POS security provider is a critical step to make sure that your POS system continues to be safe from unauthorized access. The overall consideration should be to get the best value for money based on your business needs along with the non-negotiable factors below:
- Provider reputation: Research customer reviews and testimonials, especially from businesses similar to yours, to evaluate reliability and satisfaction.
- Security practices: Ask providers about their data security measures, encryption protocols, and strategies for preventing breaches.
- Transparency: Choose a provider that openly shares information on data handling, compliance, and disaster recovery plans.
- 24/7 support: Ensure the provider offers round-the-clock technical support to address any issues promptly and minimize downtime.
4. Plan what to do in case of a data breach
Finally, establishing a swift and structured response is crucial in mitigating the damage of a POS security breach. The basics can be summarized as: Isolate – Alert – Investigate – Update – Report
Follow these steps:
- Isolate the affected system: Immediately disconnect compromised POS terminals to prevent further data loss.
- Notify relevant stakeholders: Inform IT security teams, management, and payment processors about the breach.
- Conduct a forensic investigation: Identify the source of the attack, assess the extent of the damage, and determine remediation actions. Hire a cybersecurity firm to conduct a detailed investigation, analyze security logs, and recommend further security measures.
- Alert affected customers and authorities: Inform impacted customers and employees of the incident. Provide guidance on how to change passwords and secure sensitive information. Alert regulatory authorities and credit bureaus with breach details and comply with legal reporting requirements.
Tip: Keep customers informed of the investigation’s progress and results if applicable. Consider providing affected customers with at least one year of identity theft protection services to help mitigate potential financial and reputational harm.
- Preserve evidence and track communication: Maintain records of all correspondence related to the breach, including emails, phone calls, and online chats. Retain logs of system access, POS transaction records, and financial processing data for forensic analysis and legal compliance.
- Implement security enhancements: Address vulnerabilities, apply security patches, and deploy stronger protective measures to prevent future incidents.
- Contact insurance providers: Notify your insurance company to assess coverage options for financial loss recovery and business disruption.
- Review and update security policies: Evaluate current security protocols, refine incident response plans, and strengthen compliance measures.
Also see: Point of Sale Deployment Checklist
POS security costs
The cost of POS security is threefold: Preventive hardware and software tools, PCI compliance, and data breach penalties. The last factor is often overlooked but equally important as the other two because it comprises both monetary and non-monetary damages.
Software and hardware
The following are necessary investments for protecting POS data:
- Antivirus software: $200 per year (e.g., McAfee, Norton) to protect against malware and cyber threats.
- Firewall: $100-$300 (e.g., SonicWall, Cisco) to prevent unauthorized network access.
- Security cameras: $9.99-$59.99 per month (e.g., SimpliSafe, Vivint, ADT) to monitor POS terminals and prevent physical tampering.
- EMV chip readers: $50-$1,000 each to support secure payment transactions and reduce fraud.
- Security AI & automation controls: $80-$1,500 per month for advanced threat detection and automated security responses.
- Chargeback protection services: Custom pricing, often $1,000+ per month, to help businesses reduce financial losses from fraudulent chargebacks.
PCI compliance
PCI compliance is a non-negotiable requirement for businesses that process credit card information and other personal sensitive data. The cost varies based on business size and type.
- ASV Scans: Between $200-$1,000 per year.
- QSA Services: For first-time compliance and large businesses. Starts at $10,000 based on the number of locations and network type.
Data breach penalties
Businesses that experience data breaches are subject to the following consequences:
- PCI non-compliance fees: $19.95+ monthly until compliance is restored.
- Data breach fines: From $50,000 This includes government fines and lawsuits.
- Merchant account revocation: The final sanction for a data breach is merchant account revocation, which means a business is no longer allowed to accept credit card payments.
Tip: Work with POS providers that take on some of the PCI compliance responsibilities that include securely storing credit card and customer information.
Also see: 5 Best Retail POS Systems
Impact of emerging payment technologies on POS security
The goal of fintech in developing more advanced payment technology is to provide both businesses and consumers with a faster, secure, and more convenient way to process transactions. Each new advanced payment technology is accompanied by enhanced security capabilities.
That said, it’s not far-fetched to assume that cybercriminals are working just as hard to come up with more sophisticated strategies for stealing sensitive information. US Aid reports that the cost of global cybercrime was $8 trillion in 2023 and is expected to reach $24 trillion by 2027. Half of cyberattacks affect small businesses and 59% of ransomware affects US companies.
While malware and ransomware continue to be the endgame that businesses prepare most for, social engineering and phishing are where cybercriminals tend to gain the upper hand. This is why educating consumers and employees on how to safely share their information over the internet should have equal priority in every business’ POS security strategy.